How can I verify that SSLv3 protocol is disabled?
SSL-Session:
Protocol : SSLv3
Cipher : AES256-SHA
Obviously your server still has SSLv3 enabled.
If you successfully disabled SSLv3 openssl s_client -ssl3 -connect ... should get something like this:
...SSL3_READ_BYTES:sslv3 alert handshake failure:s3_pkt.c:1260:SSL alert number 40
...SSL3_WRITE_BYTES:ssl handshake failure:s3_pkt.c:596:
...
Protocol : SSLv3
Cipher : 0000
The indicator here is that you get no cipher ("0000").
As for the ciphers itself you don't need to make any changes.
just for completeness:
testssl.sh is a nice, console-based tool to check ssl-setups of any ssl/ts - enabled servers, in oposite to ssllabs
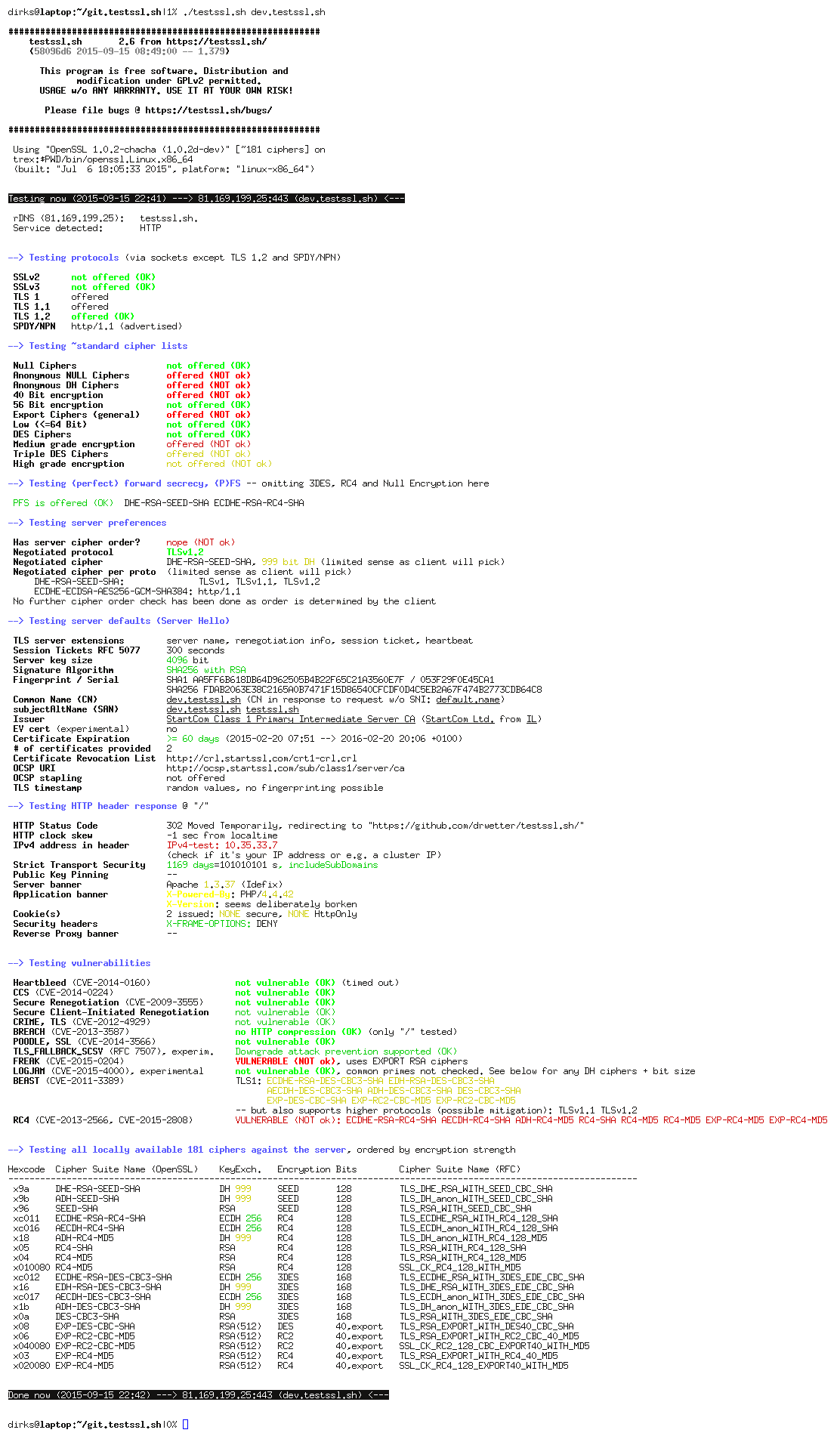
Two ways that I know of:
If you have Webinspect, they have a check specifically for this.
The simple way is to uncheck all protocols in IE with the exception of SSLv3 and see if you connect to the website.
